Sree Iyer: Hello, and welcome to Prime Time PGuru’s. This is a special broadcast with Sridhar ChityalaJi. We are going to talk about the United States disruptive forces at work. Stay tuned fastens your seatbelts. This is going to be one heck of a ride and we’ll start with welcoming our guest of the day Sridhar ChityalaJi. SridharJi Namaskar and welcome to PGurus Channel
Sridhar Chityala: Namaskar and good morning to everybody or good evening or early good evening to you all.
Sree Iyer: Wherever you are, and a lot happening over the weekend and this broadcast is going to be looking at the data that has emerged in the last few days. We have tried to put together all the things in one easy to understand format. We hope that you get your time’s worth and feel free to send us questions or any clarifications you may have, I’m not sure if we’ll have time for answering questions, but we have a lot of data to cover. With that said SridharJi, take it away. Let’s start with the 36-page Peter Navarro report.
Sridhar Chityala: Yes, sir, it’s fascinating that he calls his report a 36-page report, which is extremely well articulated. By the way, if you want to know who Peter Navarro is? Peter Navarro is the trade representative for the US Government. He’s the principal negotiator with WTO and he is also the principal negotiator with China. So, the bilateral trade conflict that is going on and in terms of coming to a conclusion. It is Peter Navarro who is representing the United States on behalf of Trump. So, he has assembled a very nice 36-page report, it’s available, it is public and we have covered several of these topics through our daily discourses or daily presentations and the data is assembled. It’s a data that is assembled from several cases over 52 cases, affidavits, etc, etc, which you can see in the report. He has put a 6 by 6 matrix and that I call it as the context matrix. The context matrix defines the six states battleground States as columns, Arizona, Georgia, Michigan, Nevada, Pennsylvania, Wisconsin, in the right order, which is alphabetical order, so, that’s on the column side. On the rows, we have, what he calls is the way you find outright voter fraud. Where did you find an outright voter fraud? Then he finds that in almost all of the states barring Pennsylvania. Then, you have ballot mishandling, outright voter fraud is, you know people misrepresenting and that vote being accepted is an example of outright voter fraud. Ballot mishandling, so, ballot mishandling is an instance, which is namely when the certain ballot is received beyond time or when ballots should have been validated and declined or when the ballot should have been marked with the light pen, so, that’s ballot mishandling. You find barring Arizona all other states have ballot mishandling issue.
Then, you have contestable process false, right, the contestable process false is that we have witnessed this and this was visible across all kind of six states as an example when Republican observers are absent you could begin to continue to kind of count, that’s one example, or they are being denied proper access data Etc. Then, you have equal protection clause violations, which is namely to state that whether the law was applied equally, to either party that have been that is being contested in the courts. Then, you are voting machine in the irregularities; the less said the better because the Dominion and Smartmatic have been at the centre of the controversy. So, you know borrowing Wisconsin you find that this is prevalent right across the five states. Then, we have these whole aberrations around patterns of switching or patterns of the allegation that could have been induced through this USB drives or some kind of external pattern external intrusions, you know, for example, the Roti Morgan, Dr Nas, you know, they all kind of comment around this abnormalities in the pattern that was also discovered in the presentations to various state legislatures. So, he kind of has tabulated this 6 by 6 Matrix and presented a contextual overview which lays the framework that two other charts which are of relevance here. The chart that is of relevance here is let us know, SreeJi when you can change it.
Sree Iyer: Sir, I just changed it.
Sridhar Chiyala: When you look at that specific chart, the second chart is about, what was the vote count on the midnight of November the 3rd? What was the vote count in the four battleground states, right?
In Georgia, Trump was leading by 357,000 votes, Pennsylvania 555, Michigan 293,000 and Wisconsin 112. That means when you look at those numbers effectively means even assuming that the postal ballots had not come in, some of those things had not been counted, etc. etc. So, you find that when you come back to today or 15th December, which is the one day after the certification occurred which is 14th December, one day after the certification occurred, you find that Biden was in the lead by 11,000 votes, Pennsylvania by 81,000 votes, Michigan by 150,000 votes and Wisconsin by 20,000 votes, They are ordered manual will recount, etc. etc. So, he called it the great tide from red to blue happened past midnight. That is the whole kind of contest around the specific election. So, could this have happened in this significant kind of a manner because the next chart, which is the chart then we kind of discussed this little more?
Sree Iyer: Yes, I put it, sir.
Sridhar Chityala: When you kind of take a look at this chart, there are more charts, but that’s ok, we can’t kind of go through all. The next chart tells you by state the margins and then it tells you, what are the possible legal ballots or errors that is visible under this category? Then he gives you around each of those five segments,
This is one we are covering so there’s greater than possibly 100,000 ballots in Arizona in question. So, even if you have a 20% strike rate of 30% strike rate, you know, Trump can easily win. In Georgia greater than 400,000, well, this is when, if you recall that we were talking about suitcases coming in, we’re talking about USB drives, you know, we were talking about also this dropbox ballots, which has not been accounted for more than 500,000 in terms of the digital record keeping. Michigan, we don’t know because you know that needs to be evaluated. Nevada is greater than 100,000, this is all, dead people voting, people from out of station voting and also people with incomplete ballots accepted etc, Pennsylvania is the massive one, you know, Pennsylvania is greater than 600,000 and to my knowledge, there were more than 1.2 million votes were under contention. Then, you actually go to the final one, which is Wisconsin, that’s greater than 200,000. What is the dimension, it is that whichever ways you slice dice and cut this stuff across in his report? And by the way, there are more than 50-60 references that are quoted like a research publication for people to kind of look at. Even if somebody believes that all of this is wrong the law of normalcy and the law of invalidating a thesis is only by revalidating and confirming the opposite, by just simply dumping it and saying it’s not. This is his case, this case is I have produced this report, I’ve Consolidated, I’ve references, this is my data point, now rebut. But, don’t decline it, you use the word, brute majority. Now, in this case, you have used arbitrariness rather than the brute majority. And so, therefore, his contention is I have produced a report. And yes the data that’s available and it’s up to you guys to say, this is prima facie. This looks something fundamentally wrong.
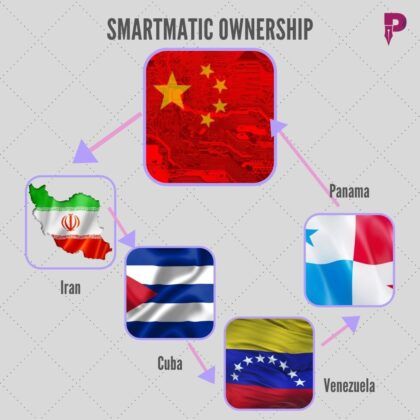
Sree Iyer: Thank you, sir. And let’s take a quick look at the next point that we wanted to bring which was essential before I go to the next point, which is the Director of National Intelligence’s report. I would like to touch upon one of the things that were used to try and compromise the political lawmakers of the United States and the person who uses That is oh, I’m sorry. I take that back first. I need to talk about one of the software’s that was used to tabulate in dominion systems and that software’s name is Smartmatic. And this is a different document that looked at how the Smartmatic ownership is and they traced it starting from China, it goes Iran, it goes to Cuba it goes to Venezuela, then it goes to Panama and then there is a Panama company by the name Smartmatic and then that comes back in. Why this obfuscation and all this software is being used inside the Dominion systems. Why do they have to have such a roundabout relationship? Who is exactly the owner of this company? Nobody has been able to predict this but we expect that those who know how to decode through shell companies and layering will be able to figure this out. We just wanted to put out, what we know thus far in terms of what is there about Smartmatic? There is one other company also that’s going to be talked about and we’ll come to that in just a minute. Let’s also take a look at the next slide, which is the foreign interference – Director of National Intelligence John Radcliffe. He confirmed I think it was a December 3rd interview or perhaps even later than that, he said that there was foreign interference in the November election, sir. Could you expand on this a little bit?
Sridhar Chityala: Right, just to kind of summarize in a SreeJi’s point, he nicely laid out. We gave the Peter Navarro then, he kind of cut transitioned with the whole kind of the ownership and the in the Dominion software kind of the election system and questions around that. So, when it comes to the next point, which is namely once on December 14. The elections were certified and sent with the Dual electoral votes with dual electoral votes now from eight states, right? So the question that came up is the next deadline, which is December 18th. The December 18th deadline, there is nothing called as deadline, but it 45 days to an Executive action, order that was passed for the National Investigative Agency to produce a report, to say was if there in foreign interference. Around the 18th Mr John Radcliffe, the head of NIA made a specific comment and in his interview. Yes, there was four in the election interference in this and this will be presented, it won’t be on the 18th. It is being validated with few other intelligent agencies to get them in a consonant. So you cannot be just sitting in making a statement, right? Adjacent to that is one has to go back again to the data, December 3rd his article which was posted in the Wall Street Journal. There is also It is also your copy of the video of his interview.?
The question was posed to him is China and national security threat? This is the question that was posed to him. His immediate answer was China is not only a US national security threat, but it is a security threat to many democratic nations around the world. It is a threat to democracy in this way his words quote unquote threat to democracy and he outlined three specific threats that they post-economic, technology and security.
Sree Iyer: Sir, the December 3rd article is available on Wall Street Journal those of you who have a subscription can look at it. And there was also another article that explains a few things of this report in Epoch times that is dated on December 17. I am just putting these dates out there for those who want to get additional research. We will try and include these links, but remember that some of them may require you to subscribe to them so, you have to essentially subscribe and then you will get the data. So let’s move on to the other one, which was essentially usage of solar wind software. This is the other one that we talked about and there was a statement by Trump, I put that slide up, sir, where Trump says voting machines have been breached by solar winds hack during the election.
Now, viewers, you may have heard about solar winds. It’s been in the news for perhaps, not exactly the best reasons that they would want. I think 400 of the 500 Fortune 500 companies. This is a big company and there was a breach and you saw last week, I think or ten days ago Google had a massive outage, where all Google apps, YouTube search engine, Gmail everything was down, Google Play was down. So, again in that also solar winds came in so perhaps, you can add a little bit more sir, on Trump’s observation that the voting machines may have been breached by solar wind during the election.
Sridhar Chityala: Well, I think that it’s very interesting that he has been very emphatic that it was the solar wind. By the way, there was also your raid on this specific company the details of which are not known and the whole inference that is coming out of this is when you see patterns of switching in the voting, which was observed in at least four states in real-time, Wisconsin, Nevada as well as the most conspicuous one, which is Georgia. They were saying these things and there was also the observation that was made that these voting machines were connected to open live internet connections during that period of time. So, where did the connectivity go to? They have not yet decided, whether it is the solar wind hack that resulted in some of these recalibrations. There was also if you go to Peter Navarro’s report some of the things that we have observed, there were breaks, for example in Georgia, there was almost a close to two hours break when things were happening when Republican observers were not present. So, the focus of the investigation would be around the connectivity between this hack as well as what happened to the systems. Dr Nas has also confirmed that basically, the software is easily breachable, the software has had a prior record of hacks and breaches. So, therefore the vulnerability of the system for such data manipulation exists and this is confirmed by the forensic analysis that was done by the data analyst. If you remember Michigan constituted a forensic audit and a forensic reporting. Georgia has not yet made that public whereas the case of Michigan, they made it public. The report very categorically, by these PhDs and data Sciences in the computer, they confirmed that the data was manipulated. So, whether you call a hack to steal the data or whether you call hack to manipulate the data, they seem to have been this vulnerability and the only reason why this solar wind comes up is that seems to be the security platform that connects the ties around the Dominion architecture. So, Trump confirms that that was the case and to make this confusing around the same time why it is, one cannot put their hands. They were also Russian hand going on, they were hacking the Commerce department and the treasury, so immediately one concluded whether this hack was actually instigated from Russia rather than from this. So, it’s very fascinating as to how all these people kind of ganging up together. But, what is equally frightening is how they can change the course of Destiny of a nation very illegally. If this were proven to be true and if the connectivity and connections are established such events occurred and in the absence of any investigation, it only leaves the door for questions and it opens the door for more such events to occur around the world.
Sree Iyer: And those of you viewers, who may have been following the news, you may have come to know that Joe Biden has again being stopped from getting military briefings. I think, yesterday or day before yesterday because there is something that has evolved. So, what all we are trying to say is this is an extremely fast-moving situation, the preponderance of data that is being submitted for viewing requires people to deliberate, they have to deliberate soundly, they have to carefully understand all the things that are at play, who’s going to call what charge? Who’s going to make the decisions? All these people it becomes very very important for them to have a calm data-driven, fact-driven an analysis to come to a conclusion and we will see what is going to happen. There is more to come. I just wanted to kind of step in a little bit to add give SridharJi, a breather so that he gets a chance to get his thoughts back. So, SridharJi, let’s go to the next slide and this has to do with the alleged Chinese spy. Now people are beginning to drop the word alleged. So, it is becoming more and clearer that Christine Fang or Fang Fang was associated. We have pictures now of her being taken with many many mayors in the Bay Area Dublin, Livermore, with the then Mayors, there’s, of course, Dublin, Livermore, Fremont and then, Congressman such as Ro Khanna and Eric Swalwell and Ash Kalra these are all the pictures that have come out there and now people are beginning to start asking questions. Now, there is also a big reveal that, I think, the then Mayor of Ohio, there is one news report that that person was indeed caught. So, again other people are saying a couple of Midwestern mayors. The point here is there’s a systematic way in which this has been done. So, this kind of tells you, that this is just one person but, also blows the mind is when news of her being exposed came. How was she allowed to leave in 2015? I mean FBI knew this, they evidently had conversations with Eric Swalwell, that look the person that you are associated with has all these challenges. I’m sure they had these conversations with the other people were lawmakers. And yet, how did she leave? So, this is another interesting question that I hope sometime the answer will be told as to how this person was allowed to leave the very very loose relationship in the sense that the person comes to California State University in Hayward. It is one of the 30 plus State University’s that California has, one the highest number of state universities. She was enrolled as a student there, but suddenly she is found in all sorts of campuses. She’s in everybody’s chair. She’s bringing in, you know donors, who know what all. You can write a book about this person’s involvement in what happened. But anyway, I just wanted to put it out there. All this data is coming out fast because one people wake up. Oh, I’ve seen this person somewhere and then another story comes out and so this is also another thing because it is mostly around the Bay Area. It’s a lot of interest to those of us, I also live in the Bay Area to know more about what you are lawmakers really do. So, sir, let’s go to the next slide, which is the influence of Beijing in educational institutions, how they try to create the mindset of the youth by trying to say, why it is there? What the political ideology that comes out? So, can you tell us a little bit about this because I think there were a few statements that were made by the Secretary of State Mike Pompeo about this?
Sridhar Chityala: Yes, I just want to transition by saying, you know bees flock to the hive which is loaded with honey, sir. So, therefore there’s no surprise that lots of bees seem to have flocked to the Silicon Valley. There seems to be a lot of the deposit of honey located that’s one thing and the second, I mean just going to transition into your specific question. Well, a China has a very orchestrated type of a program in terms of you know, we had reported this in our show of both on RCEP overview as well as the rise, the rise and the rise of China. They were very very orchestrated program basically to control everything right from education right from the college and school, that is basically the thinking process which starts in the education. So what you find is that two specific examples, one is that we have this what you call in South Africa, they have a program where you find amongst these 101.85 billion people who have been scattered, 1.85 billion, 1.85 million, sorry, 1.85 million people, let me correct myself was scattered across the globe in various institutions government, government agencies, enterprises, corporations, and so on. So these people basically advocate this law of communalism and law of command and control and why this centralized power structure is the way to go. So this particular logic is embedded in enshrined into the thinking process and that is fed through the college system. So that is basically saying that ‘here is the way we do it’. So one specific example that is given is the education that is a joint collaboration between South Africa and China.
The second example, which Mike Pompeo is pointing out is that he’s singled out MIT then subsequently he talked about Yale, he talked about Harvard, he talked about Georgetown, he talked about Georgia Tech, he talked about Stanford. So he’s basically speaking about at least now six to seven institutions. He says that the endowment awards not just China but done by even Saudi as well as Russia is an astonishing number $6.5 billion is the number, that’s public record, and he has stated that these people have not reported the volume and the amount of money that has been received. Mind you many of these colleges or imminent schools also run off-campus programs all around the world. Notably, there is an NYU in China. There probably are other schools in China as well. Very similar to NYU. Yes, sir.
Sree Iyer: I think the news has come out now that the Vice-Chancellor of NYU, Shanghai is a Chinese Communist Party member.
Sridhar Chityala: Correct. That’s a very good interjection, which is namely yes, he is a CCP member. So I think once you kind of deep dive into each of these data, by the way, these 1.85 million names are being released. I think 37,000 names has been released also Wikileaks has released full data in anticipation of Julius Assange getting his full file is available. To respond to your question, Pompeo is saying we really have a problem if they begin to alter the mindset of our own students and also just adjacent to it which is covered by John Radcliffe in his national security threat issue recently is a professor, the head of the chemistry department was actually caught and is supposed to have not reported, you know saving $150,000 dollars a month, for potential leakage of academic data, academic research programs. So the academic institutions have become a battleground in winning the mindset of the theology or the philosophy, and when you look at the United States, there is rising socialism and rising communism in the educational system, and no less a person than John Trooper, the retired Wisconsin judge who has posed a question, which just came in the Press today and which is to say today that the courts, the legal system, and even the witnesses are reluctant because they are witnessing direct threats from left. So, therefore, we are unable to enforce any of these things. So the academic system seems to be on the way in terms of, unless it is stopped, is well on the way in terms of re-architecting the way the US education system is going to be trained very much to the get to the needs of what happens in the Chinese Model.
Sree Iyer: I want everyone to take a step back and reflect on what Sridharji has just said. What is it that most parents aspire for the children? They want them to go to Harvard, they want them to go to MIT, they want them to go to Yale, they want them to go to Georgetown University. They are trying to pursue a career in law and these are the universities where the might set adjustment about socialism being good is being propagated. I can tell you that this if it is not stopped or at least the truth doesn’t come out then you’re going to have the whole world awash with socialism and let me ask you this question for so those of you who left socialist countries for the West. What is it that you found stifling there? What was the reason for you to leave your home country to come to the West because you felt that the West gave you opportunities? They gave you full freedom for you to find your potential. That’s what they found and now if this continues, in 15 years I can tell you the whole thing is going to turn on its head and suddenly the whole world become will become socialist. And I don’t think that is something that is good because socialism assumes that somebody is doing the work it just tries to spread the money out of that to everybody so if everybody becomes a socialist and who’s going to do the work, that’s the question that people will have to ask and socialism doesn’t have an answer for that. They just go back to say that ‘Ah, you make too much money. That’s all they answer.’ Anyway, that’s just my rant sir. Let’s go to the next slide,
Sridhar Chityala: Can I just make one observation? least citizenship? In 2019 as part of the 70th anniversary of its rule, this is 1949 formation of under one single monolithic structure so the Chinese policy states, which is effectively it strengthens ideological control, particularly in higher education, among religious and ethnic minorities and within the bureaucracy. It has devoted massive resources to technologies such as social technologies, which do social control, artificial intelligence, Biometrics and other types of technologies which monitor and shape the minds and behaviour of its own 1.4 billion people. What it wants to do is leverage those things and apply them around the world, I forget the name of the FBI director, one of the directors who made a very specific point around this where he says the United States will not face threats, which puts its existence your stuff, in the way of warfare, it is going to be an anonymous threat which comes in these forms what we have seen elections, education, espionage, compromises of the ecosystem and creating mischief and nuisances around the security parameters, trade disputes etc. So it has practised this process which, by the way, you can go back and look at what they proclaimed in 2019 as part of the 70th anniversary. The data is available for people to go and see it. Sorry, sir I just wanted to put that context around it.
Sree Iyer: Not at all, sir. I just put the slide of Mike Pompeo talking about various universities where the Chinese pressure was being faced to not criticize China too much. So this whole thing about fake narratives, now you have beginning to see who’s behind all this. So, almost all the roads seem to appear to lead to one or two countries one of them being China. So it’s for you viewers to form your own conclusions. All we are trying to tell you is there is data available out there. You need to look for it. We’re going to provide a few links. I’m not sure we’ll be able to provide you with all the links. Certainly, I must tip my hat to Sridharji for the extraordinary amount of research that he has done in putting together the slides that are being shared today.
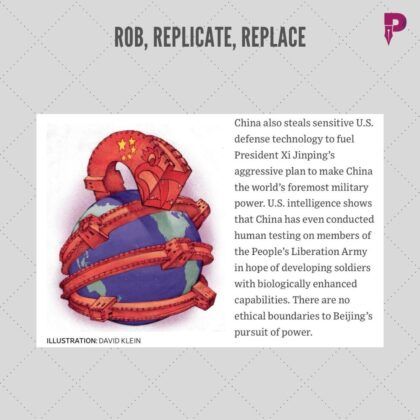
So, with your permission, sir, I’d like to go to the next slide and I’ll tell you the context. This is about the overall philosophy of China the 3 R’s Rob, Replicate and Replace. Now, this is playing out in our lives today gentlemen, you go and start looking in Amazon to find out some of the most common household items that you normally use and you will be surprised to see how many new names hard to pronounce but you will be surprised to see how many new options are being made available. Sridharji, this is a very important topic very close to your heart and my heart.
We are inventors, we have seen The Cutting Edge of Technology we Understand the pain that goes into getting some technology done, getting the intellectual property around it, getting the patents issued, and then when the design moves to China there is no way to enforce it. So that is just one of the problems. So let’s take a look at it a little bit deeper. Take it away, sir. Rob, Replicate, and Replace.
Sree Iyer: Correct. This is again, December 3rd report that you will find, the observations from December 3rd report as John Radcliffe deep dived into the activities and they began to find and which is presented by the both the House and Senate intelligence committee. So the story is that they found that it is a very very carefully orchestrated program in terms of two specific domains one is around technology and the second is around IP and patents and capabilities around new industries. So the objective is you first steal it then you replace it, you rob, you replace and then you replicate? Okay. Now I’m not going to mention some of the names that you know, when you look at large dominant players in the Chinese ecosystem, right and then you can infer in your own way, where their origins came from. Now let’s look at R, R and go into the third R, which is namely the recent controversy that surrounds the inventions by their own people like Jack Ma around be it financial which was to be the largest IPO or be it Alibaba or anything to come, they have now imposed prudential controls and ownership around the oversight and management of these technologies and effectively stated the last R the old governing principles do not work, the Constitutional framework and the principles of CCP should be applied. So this is the contest that is going on between the entrepreneurs within the Chinese ecosystem themselves in the last R. That’s just one example of what you can infer.
There’s a specific instance that Radcliffe has, there’s quite a few but let me take one. This is the Sinowell, the wind turbine technology for a superconductor, how that was taken and how the information was transmitted. He says the cost of the transmission which is Robin replaced is probably a billion dollars, but when you replicate and roll it out the cost can be quite significant. And of course, that thing was banned. That’s an example where they take a specific case study on how it was done.
There’s a second example that is given. You have several Chinese companies with American employees. There we find that think of this as a hypothetical case, basically what he’s saying is okay, now you find that some restriction is placed on the behaviour of this particular company when a restriction is placed on the behaviour of this person-specific company and they go on to basically state that they use the people employed to influence the congressman or congresswomen in that specific constituency indicating that look their jobs are under threat if she is not amenable then she’s not going to get votes and this is cited without mentioning anything as a second example.
The third I already touched upon, the Industrial Research Espionage and one of the professors being arrested. We’re not going to mention the names and everything. You can go and research it’s all available. This is 2020 kind of an issue. So this is the whole concept of, surreptitious, robbing replacing and replicating with an intent that you dominate. This is the whole contention around the 5G technology as well. The 5G technology, nobody wants to be a manufacturer or a component maker associated with 5G, but they also don’t want anything to do with Chinese technology. There are more than 40 companies which again we have covered which have an association with some manufacturers of metals also suppliers to companies like Boeing, those companies have now been banned or barred from actually working in the United States by President Trump.
So these are examples, John Radcliffe goes on to say that there was not much initial focus, much initial focus was diverted somewhere else. Close to $85 billion has been allocated now targeted at looking at how these incidents and instances pose a direct threat to the functioning of theUS system, eventually the global model.
Sree Iyer: Before we move from this slide, I just want to read this text that is there. I don’t know how many of you can read it. So I’ll read it out for the benefit of our viewers. China also steals sensitive US defence technology to fuel president XI Jinping’s aggressive plan to make China the world’s foremost military power. US intelligence shows that China is even conducted human testing on members of The People’s Liberation Army in the hope of developing soldiers with biologically enhanced capabilities. There are no ethical boundaries to Beijing’s pursuit of power. Sir, this is a very very telling statement coming from John Radcliffe and this again is in the Wall Street Journal article of Dec 3rd. I think there is a fair amount of data that we have placed in front of our viewers to assimilate, to understand and then you make your own conclusions as to what exactly is at play here. This US Election was but an event luckily for the world, for the United States, for those of us who are interested in a thriving democracy trying a thriving democracy world. Now, we are beginning to see one place where perhaps things are not as watertight as they wanted it to be, these are now coming out. So I would take it likely at my own risk because sometimes these are seminal events in history. If you don’t grab the opportunity at the right time, then the whole history gets changed forever in the wrong direction. Sridharji, now, I think we have finished all our slide presentation part and I’d like you to give us a little bit of your overview. So now we have shared all the information that is out there thus far what is going to happen next? How do you think these are going to move forward? What exactly is the world looking at? Now, remember that we didn’t mention one word about the 800-pound gorilla in the room – covid and where did that originate from? China. See, there are just too many coincidences here for you to say, ‘Oh that is coincident. This is coincident.’ Don’t become apologists, seek the truth. Sir, I’d like you to now summarize this talk. We are about 45 minutes into the talk, and if you could just take a few minutes to summarize it and then we can call this a done deal.
Sridhar Chityala: Great. But I think that one observation as I transition into the summary, this is the oldest, the United States is the oldest democracy. The largest democracy is also facing a very similar kind of use case test that is going on. And the largest democracy being in India. And if one looks at India and the adjacent ecosystem of India, which is what’s going on in Nepal, what’s going on around in Bhutan, what’s going on around in Ladakh! What the Chinese did, what I call in a very very deceptive manner that has just now come out in Canada and Canadians know practising at the invitation of Troudeu without the Canadian Forces permission, practising is always that already gave people, practising on the in the snow mountains the warfare. Basically, who is the target? India is the target. What is the location? Ladakh is the location. All kinds of influences that one is seeing you may see in different forms play out in India and they are visible signs of that. So I think that’s just something for people to kind of Digest. This is a very good playbook in terms of what is to come there. So if I summarize I think that you know the United States is under many formats of Siege, or many formats of intrusion and what shall I say layers of influence we forgot to talk about how they use media. Gordon Chang has given a very detailed note around how media is used. So then they don’t leave anybody, you know media, government, enterprises, corporations, educational Systems, how every tool that is available is kind of used. So, where are we today? Today, we are at the stage where the elections are moving through this legal process and legal local stuff is going on.
The Supreme Court stuff notwithstanding the fact it is dismissed but it still is in contention at play. So we will now inch towards the January 6th deadline, the January 6, not deadline, January 6 Milestone. So the January 6th is the milestone where the House and Senate meet and they regroup, they discuss, debate, look at the votes that are cast, assess and basically determine the next course of action. The next course of action is several. Now senators and house representatives from the Republican Party have raised questions and concerns around the validity of the election and around the integrity of the election. All it requires is one House member and one Senate member to stand up. So you’re going to see that drama played out on January 6th. And if it gets into a vote, there is a constitutional provision on how that gets reviewed and how that gets processed. So I see that the legal process going concurrently, I see the Constitutional process of the January 6th, and that will eventually culminate on January 20th. Even assuming that everything is hunky-dory and January 6th everybody has stated that constitutionally there is still time between January 6th and January 20th to overturn either through state legislatures or Supreme Court. The indications are the Supreme Court may or may not choose to get entangled. There were a lot of rumours floating around that this investigative agency reports will be taken and some kind of Martial law will be imposed in this Six States and I think everybody from the army to the president himself as debunked this report, which is to say, there’s no such kind of thought process that is even contemplated. So the whole concept of NIA is to make public aware, make the House and Senate aware as to what exactly has transpired so that their integrity of the electoral system in the Republic can be preserved as well as the read the electoral system needs reforms. I think that in one thing has come out very clearly the electoral system needs a reforms. What are the Electoral College will prevail or whether the from Electoral College will move into the absolute voting which is namely across the Nation, Who’s got the majority-minority? Would that be the pattern? So it’s a straight-up or down vote is what everybody is trying to push for? I doubt I very much doubt as part of the Federation whether the United States would move to that. It will have better integrity and its systems and software and the voter registration process and voter ID and even technology coming in a much more active manner, but I just don’t see the electoral college being abandoned big which is the sanctity of this conformation of the Federation, but I could be wrong.
Sree Iyer: Thank you very much Sridharji. That was a wonderful summary of what happened. And what is perhaps going to play out in the next few weeks, stay tuned. We’ll be back again tomorrow same time on PGurus online channels YouTube, Facebook, and Twitter and thank you for your support. Please do not forget to subscribe to our channel. Please refer us to your friends and family. We want to get to 1 million mark as quickly as possible and it will not happen without your support. Please donate to our cause. As always thanks to Sridharji for donating and dedicating the time that it took to put together this presentation and like we said we will try and share some of the links that we have used to come up with these findings and you can read and get acquainted with this whole process. What is at stake is democracy not just for the United States, but for the whole world. Thank you very much, Sridharji and we’ll be back tomorrow. Same time, same locations. Namaskar.
Sridhar Chityala: Thank you Ji, and have a wonderful Sunday evening to those its evening and wonderful Sunday for those who are in the United States.
References:
1. DNI John Ratcliffe Confirmed There Was Foreign Interference in November Elections: Report The Epoch Times – 17 Dec 2020
2. China Is National Security Threat No. 1 – Wall Street Journal – 3 Dec 2020
3. Beijing Using US Newspapers to Promote ‘Insidious Narratives,’ China Expert Gordon Chang Says The Epoch Times – 7 Dec 2020
4. Suspected Chinese Spy Spun Web of Influence Among US Politicians: Report The Epoch Times – 9 Dec 2020
5. CCP Members Hold Positions at British Consulates, Major UK, US Firms: Leaked Database The Epoch Times – 13 Dec 2020
6. Pompeo unloads on US universities for China ties AP news – 10 Dec 2020
7. Former Wisconsin Judge: ‘Our Court System Has Been Deeply Intimidated by the Left’ The Epoch Times – 20 Dec 2020
- Rahul Hood read the Right story (Robin Hood) but applied it to the wrong oppressed - April 24, 2024
- Xi Jinping treats Chinese people like Ganna (Sugarcane) – Squeeze them & throw them away! - April 9, 2024
- Tharoor Aadat se Majboor - April 7, 2024